imx6ul之OpenWRT中使用无线网卡做中继器与AP热点+ A1 g2 R9 l1 V2 ]/ B% `
' \; b% ~( L& a- ?4 Y- s+ Q
中继器与AP的实现这里我们假定中继器完成下面这样的一个功能: Wired Network ---> Wireless Network ---> 上级无线路由器3 x2 c* G0 l% m) L3 ?
即从外部插入一个网线,通过imx6UL上面的无线网卡将数据转发到上级的路由器上面, 当然也可以完成下面这样的传送:
}2 Q8 F5 l( A* i5 o4 \7 a Wireless Network(AP mode) --> Wireless Network(Client) --> 上级无线路由器
& W \+ U8 }! [# I7 n* O$ G1 ]
即设立一个AP热点,相当于一个路由器,然后再将这个AP的数据通过另外一个无线网卡转发到上一级的路由器或者WLAN上面。 用图片来表示如下: 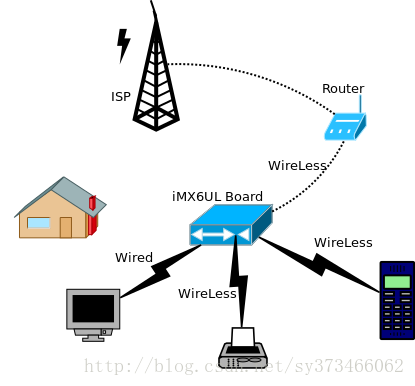
! Z* M" T4 {% i- m要完成这些功能, 我们需要: - 1. 驱动无线网卡
- 2. 建立AP热点
- 3. 其中一个wired或者wireless介入到上一级路由器或者WLAN中
- 4. 使用IPTables来对数据包进行转发' A0 m- Z3 }) T7 y6 P/ ^
- Z( b9 ^" ~' z- a; G/ \
对于1,我们在前面已经完成,对于Wired Network访问WLAN我们也已经在前面完成。所以这篇我们将完成2与3, 以及4。
- H8 y- E+ S9 h6 m% c, B
AP热点的建立建立AP热点,我们使用经典的Hostapd工具来完成, 这个在OpenWRT中已经存在, 直接选上,然后build即可。 Hostapd的使用
1 Z* c8 d/ z" ^* J. b2 q5 G( l然后我们可以查看对应的使用帮助 [plain] view plaincopy
1 o& |. p) k+ n, X# `1 h* b" v: M
|: d9 @! \9 z e: I Y# }: s
( ~- n5 x! q+ Q7 R, _( u Y+ c' Q- root@(none):/# hostapd --help
- hostapd: invalid option -- '-'
- hostapd v2.5
- User space daemon for IEEE 802.11 AP management,
- IEEE 802.1X/WPA/WPA2/EAP/RADIUS Authenticator
- Copyright (c) 2002-2015, Jouni Malinen <j@w1.fi> and contributors
-
- usage: hostapd [-hdBKtv] [-P <
 ID file>] [-e <entropy file>] \ ID file>] [-e <entropy file>] \ - [-g <global ctrl_iface>] [-G <group>] \
- <configuration file(s)>
-
- options:
- -h show this usage
- -d show more debug messages (-dd for even more)
- -B run daemon in the background
- -e entropy file
- -g global control interface path
- -G group for control interfaces
- -P PID file
- -K include key data in debug messages
- -t include timestamps in some debug messages
- -v show hostapd version
+ \9 M: g% f/ ^
" |. ?; i. {& T# n4 g/ J. v
$ W" U! l; b# ?, S: b# Y7 r因此可以确定需要一个config文件, 这个configuration file我们如下填写:
% U9 _1 o( M" v( y/ Y[plain] view plaincopy
6 _- x; w, T/ L' ?. ]4 }. U4 ~! u. V3 k L, H" d- H9 d2 C. @
4 ]( {0 x* }& B, n" Q' _
- root@(none):/# cat /etc/hostapd_ori.conf
- interface=wlan1
- ssid=TonyOpenWRT
- channel=9
- hw_mode=g
- ignore_broadcast_ssid=0
- auth_algs=1
- wpa=3
- wpa_passphrase=TonyHo123456
- wpa_key_mgmt=WPA-PSK
- wpa_pairwise=TKIP
- rsn_pairwise=CCMP 2 Q2 i% p7 b0 N
( R& |. M& A) h& n2 _即我们创建一个SSID为TonyOpenWRT的热点, wpa_passphrase为密码, 后面的为加密方式, 然后还选择了channel, 这个channel可以通过前面的iw list来查看, 例如其中一个为:
) ], ~2 f8 h, Y, j/ p[plain] view plaincopy
7 y' f$ n' L* C# h U7 P$ H+ ?# P$ L8 L+ o2 n* _# Z) h8 K h D
6 @. C7 M! k% X" \
- Frequencies:
- * 2412 MHz [1] (20.0 dBm)
- * 2417 MHz [2] (20.0 dBm)
- * 2422 MHz [3] (20.0 dBm)
- * 2427 MHz [4] (20.0 dBm)
- * 2432 MHz [5] (20.0 dBm)
- * 2437 MHz [6] (20.0 dBm)
- * 2442 MHz [7] (20.0 dBm)
- * 2447 MHz [8] (20.0 dBm)
- * 2452 MHz [9] (20.0 dBm)
- * 2457 MHz [10] (20.0 dBm)
- * 2462 MHz [11] (20.0 dBm)
- * 2467 MHz [12] (disabled)
- * 2472 MHz [13] (disabled)
- * 2484 MHz [14] (disabled)
# | u. [8 g P
& h( f @$ u% }
! i, p/ q. m. o3 o" u% ]" u7 i s后面的【】中的就是channel了。" o' h8 ~9 t4 L6 @/ x9 m7 p
建立AP
" }( u# d$ ^; B8 o然后我们使用后台运行的方式启动hostapd,并且打开debug信息,便于我们查看: [plain] view plaincopy9 h' {7 {3 w* l. Z; B
" P: O' i! }1 N Q7 K' {
1 E% D* \$ A3 m7 f/ L* \- root@(none):/# hostapd -B -d /etc/hostapd_ori.conf
- random: Trying to read entropy from /dev/random
- Configuration file: /etc/hostapd_ori.conf
- rfkill: Cannot open RFKILL control device
- nl80211: RFKILL status not available
- nl80211: TDLS supported
- nl80211: TDLS external setup
- nl80211: Supported cipher 00-0f-ac:1
- nl80211: Supported cipher 00-0f-ac:5
- nl80211: Supported cipher 00-0f-ac:2
- nl80211: Supported cipher 00-0f-ac:4
- nl80211: Supported cipher 00-0f-ac:6
- nl80211: Using driver-based off-channel TX
- nl80211: Use separate P2P group interface (driver advertised support)
- nl80211: interface wlan1 in phy phy1
- nl80211: Set mode ifindex 9 iftype 3 (AP)
- nl80211: Setup AP(wlan1) - device_ap_sme=0 use_monitor=0
- nl80211: Subscribe to mgmt frames with AP handle 0xcfd5d8
- nl80211: Register frame type=0xb0 (WLAN_FC_STYPE_AUTH) nl_handle=0xcfd5d8 match=
- nl80211: Register frame type=0x0 (WLAN_FC_STYPE_ASSOC_REQ) nl_handle=0xcfd5d8 match=
- nl80211: Register frame type=0x20 (WLAN_FC_STYPE_REASSOC_REQ) nl_handle=0xcfd5d8 match=
- nl80211: Register frame type=0xa0 (WLAN_FC_STYPE_DISASSOC) nl_handle=0xcfd5d8 match=
- nl80211: Register frame type=0xc0 (WLAN_FC_STYPE_DEAUTH) nl_handle=0xcfd5d8 match=
- nl80211: Register frame type=0xd0 (WLAN_FC_STYPE_ACTION) nl_handle=0xcfd5d8 match=
- nl80211: Register frame type=0x40 (WLAN_FC_STYPE_PROBE_REQ) nl_handle=0xcfd5d8 match=
- [ 495.443813] IPv6: ADDRCONF(NETDEV_UP): wlan1: link is not ready
- nl80211: Add own interface ifindex 9
- nl80211: if_indices[16]: 9
- phy: phy1
- BSS count 1, BSSID mask 00:00:00:00:00:00 (0 bits)
- nl80211: Regulatory information - country=00
- nl80211: 2402-2472 @ 40 MHz 20 mBm
- nl80211: 2457-2482 @ 40 MHz 20 mBm (no IR)
- nl80211: 2474-2494 @ 20 MHz 20 mBm (no OFDM) (no IR)
- nl80211: 5170-5250 @ 160 MHz 20 mBm (no IR)
- nl80211: 5250-5330 @ 160 MHz 20 mBm (DFS) (no IR)
- nl80211: 5490-5730 @ 160 MHz 20 mBm (DFS) (no IR)
- nl80211: Added 802.11b mode based on 802.11g information
- Completing interface initialization
- Mode: IEEE 802.11g Channel: 9 Frequency: 2452 MHz
- DFS 0 channels required radar detection
- nl80211: Set freq 2452 (ht_enabled=0, vht_enabled=0, bandwidth=20 MHz, cf1=2452 MHz, cf2=0 MHz)
- * freq=2452
- * vht_enabled=0
- * ht_enabled=0
- RATE[0] rate=10 flags=0x1
- RATE[1] rate=20 flags=0x1
- RATE[2] rate=55 flags=0x1
- RATE[3] rate=110 flags=0x1
- RATE[4] rate=60 flags=0x0
- RATE[5] rate=90 flags=0x0
- RATE[6] rate=120 flags=0x0
- RATE[7] rate=180 flags=0x0
- RATE[8] rate=240 flags=0x0
- RATE[9] rate=360 flags=0x0
- RATE[10] rate=480 flags=0x0
- RATE[11] rate=540 flags=0x0
- hostapd_setup_bss(hapd=0xcfcf50 (wlan1), first=1)
- wlan1: Flushing old station entries
- nl80211: flush -> DEL_STATION wlan1 (all)
- wlan1: Deauthenticate all stations
- nl80211: send_mlme - da= ff:ff:ff:ff:ff:ff noack=0 freq=0 no_cck=0 offchanok=0 wait_time=0 fc=0xc0 (WLAN_FC_STYPE_DEAUTH) nlmode=3
- nl80211: send_mlme -> send_frame
- nl80211: send_frame - Use bss->freq=2452
- nl80211: send_frame -> send_frame_cmd
- nl80211: Frame command failed: ret=-16 (Device or resource busy) (freq=2452 wait=0)
- wpa_driver_nl80211_set_key: ifindex=9 (wlan1) alg=0 addr=(nil) key_idx=0 set_tx=0 seq_len=0 key_len=0
- wpa_driver_nl80211_set_key: ifindex=9 (wlan1) alg=0 addr=(nil) key_idx=1 set_tx=0 seq_len=0 key_len=0
- wpa_driver_nl80211_set_key: ifindex=9 (wlan1) alg=0 addr=(nil) key_idx=2 set_tx=0 seq_len=0 key_len=0
- wpa_driver_nl80211_set_key: ifindex=9 (wlan1) alg=0 addr=(nil) key_idx=3 set_tx=0 seq_len=0 key_len=0
- Using interface wlan1 with hwaddr 94:0c:6d:7c:12:f6 and ssid "TonyOpenWRT"
- Deriving WPA PSK based on passphrase
- SSID - hexdump_ascii(len=11):
- 54 6f 6e 79 4f 70 65 6e 57 52 54 TonyOpenWRT
- PSK (ASCII passphrase) - hexdump_ascii(len=12): [REMOVED]
- PSK (from passphrase) - hexdump(len=32): [REMOVED]
- random: Got 15/20 bytes from /dev/random
- random: Only 15/20 bytes of strong random data available from /dev/random
- random: Not enough entropy pool available for secure operations
- WPA: Not enough entropy in random pool for secure operations - update keys later when the first station connects
- GMK - hexdump(len=32): [REMOVED]
- Key Counter - hexdump(len=32): [REMOVED]
- WPA: Delay group state machine start until Beacon frames have been configured
- nl80211: Set beacon (beacon_set=0)
- nl80211: Beacon head - hexdump(len=62): 80 00 00 00 ff ff ff ff ff ff 94 0c 6d 7c 12 f6 94 0c 6d 7c 12 f6 00 00 00 00 00 00 00 00 00 00 64 00 11 04 00 0b 54 6f 6e 79 4f 70 65 6e 57 52 54 01 08 82 84 8b 96 0c 12 1y
- 01 09
- nl80211: Beacon tail - hexdump(len=65): 2a 01 04 32 04 30 48 60 6c 30 14 01 00 00 0f ac 02 01 00 00 0f ac 04 01 00 00 0f ac 02 00 00 dd 16 00 50 f2 01 01 00 00 50 f2 02 01 00 00 50 f2 02 01 00 00 50 f2 02 7f 08 00
- nl80211: ifindex=9
- nl80211: beacon_int=100
- nl80211: dtim_period=2
- nl80211: ssid - hexdump_ascii(len=11):
- 54 6f 6e 79 4f 70 65 6e 57 52 54 TonyOpenWRT
- * beacon_int=100
- nl80211: hidden SSID not in use
- nl80211: privacy=1
- nl80211: auth_algs=0x1
- nl80211: wpa_version=0x3
- nl80211: key_mgmt_suites=0x2
- nl80211: pairwise_ciphers=0x18
- nl80211: group_cipher=0x8
- nl80211: SMPS mode - off
- nl80211: beacon_ies - hexdump(len=10): 7f 08 00 00 00 00 00 00 00 40
- nl80211: proberesp_ies - hexdump(len=10): 7f 08 00 00 00 00 00 00 00 40
- nl80211: assocresp_ies - hexdump(len=10): 7f 08 00 00 00 00 00 00 00 40
- WPA: Start group state machine to set initial keys
- WPA: group state machine entering state GTK_INIT (VLAN-ID 0)
- GTK - hexdump(len=32): [REMOVED]
- WPA: group state machine entering state SETKEYSDONE (VLAN-ID 0)
- wpa_driver_nl80211_set_key: ifindex=9 (wlan1) alg=2 addr=0x8dc74 key_idx=1 set_tx=1 seq_len=0 key_len=32
- nl80211: KEY_DATA - hexdump(len=32): [REMOVED]
- broadcast key
- nl80211: Set wlan1 operstate 0->1 (UP)
- netlink: Operstate: ifindex=9 linkmode=-1 (no change), operstate=6 (IF_OPER_UP)
- wlan1: interface state UNINITIALIZED->ENABLED
- wlan1: AP-ENABLED
- wlan1: Setup of interface done.
- ctrl_iface not configured! 0 J6 M: F0 d% u+ Q& n
5 R1 S' x5 P. M0 H6 h
$ k; v6 f) }2 Y" t8 h( C; b其中里面用到了加密时候需要的随机数,这个是使用内核中的random节点来生成的,所以我们在内核这两个还需要添加random驱动。
8 b+ x4 G! x; z2 Y验证AP在验证之前,我们需要给我们的这个网卡自己一个IP地址, 因此直接: [plain] view plaincopy( N7 n. \3 A" z
, r# [4 o) Q! O# A9 d e( W; l/ C/ d) s) d8 V9 C* J& u5 b |
- root@(none):/# ifconfig wlan1 192.168.2.1
- root@(none):/# ifconfig wlan1
- wlan1 Link encap:Ethernet HWaddr 94:0c:6d:7c:12:f6
- inet addr:192.168.2.1 Bcast:192.168.2.255 Mask:255.255.255.0
- inet6 addr: fe80::960c:6dff:fe7c:12f6/64 Scope
 ink ink - UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
- RX packets:131 errors:0 dropped:0 overruns:0 frame:0
- TX packets:106 errors:0 dropped:0 overruns:0 carrier:0
- collisions:0 txqueuelen:1000
- RX bytes:20162 (19.6 KiB) TX bytes:20954 (20.4 KiB) ' [$ r# V+ N' W. @7 H0 q9 I
7 Y0 L( L2 A- W+ ]4 o% {8 b
; ?/ S5 o7 K3 ^2 P; J然后我们打开手机查看是否可以看到我们的热点:
% b) i/ Z! b/ g) l$ Z/ h: o; `, Y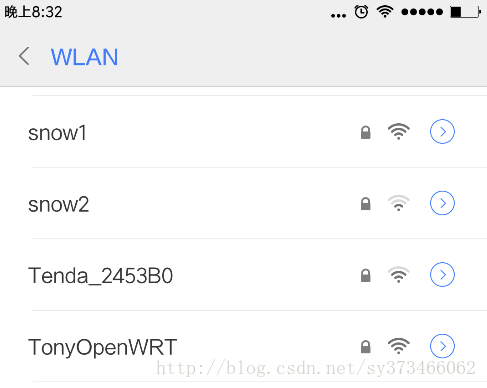 ! ]& o0 |/ d( Z3 n ! ]& o0 |/ d( Z3 n
然后我们使用手动配置IP方式连接热点
& o6 ~( \4 u$ M0 Z# P. P% [$ d! h/ a 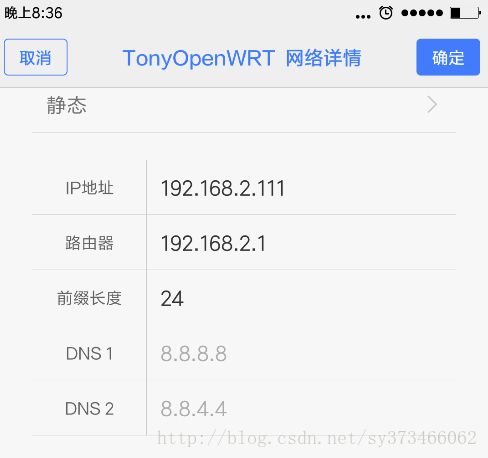
& L. k# ]6 l" M6 q: O! a% D连接完成后, 我们可以看到已经连接的状态: 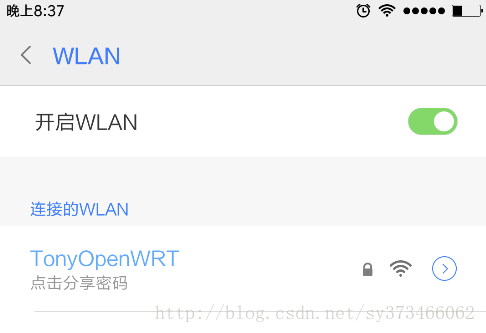
2 Y6 ]" L% _, [: \, ]3 o5 X& O然后在手机上面可以Ping一把确定是否连通: 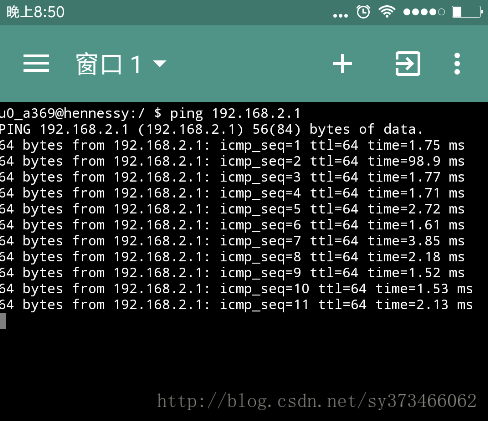 " b* n- q: t7 p: W, p; M- r+ s& f " b* n- q: t7 p: W, p; M- r+ s& f
然后在iMX6UL上面也来ping一把这个手机: [plain] view plaincopy* B" K( M' C2 K% g
5 y6 R7 q. o( ]" D2 D) B
- x( l% q5 t: S+ a* K" x6 Z- root@(none):/# ping 192.168.2.111
- PING 192.168.2.111 (192.168.2.111): 56 data bytes
- 64 bytes from 192.168.2.111: seq=0 ttl=64 time=90.952 ms
- 64 bytes from 192.168.2.111: seq=1 ttl=64 time=143.093 ms
- 64 bytes from 192.168.2.111: seq=2 ttl=64 time=4.508 ms
- 64 bytes from 192.168.2.111: seq=3 ttl=64 time=46.859 ms
- 64 bytes from 192.168.2.111: seq=4 ttl=64 time=2.539 ms
- 64 bytes from 192.168.2.111: seq=5 ttl=64 time=2.697 ms
- ^C
- --- 192.168.2.111 ping statistics ---
- 6 packets transmitted, 6 packets received, 0% packet loss
- round-trip min/avg/max = 2.539/48.441/143.093 ms $ K: {% O. |5 y5 H4 |4 |- V% `# |
4 x/ N* z* L3 T; d3 q
! B/ K* n8 v0 C, ^至此,基本的连接就好了, 如果想要自动获取IP地址,那么我们还需要配置DHCPD。4 h" d7 `8 e7 x# C6 A' v/ T: `! K
1 ^! c+ f2 Q/ u. }6 r" @
wpa_supplicant的配置前面我们使用其中一个网卡,配置好了AP, 接下来我们使用另外一个Wireless作为上一级router的接入设备。 这个可以参考我以前写的文章: Yocto i.MX6 (TQIMX6) (03) : wifi网卡的相关工具wpa_supplicant与dhcp 9 Q5 `5 d' p! v- V! H# f: P
但是wpa_supplicant的版本升级后, 和hostapd的使用基本一致起来, 因此以前的使用方法稍微有些不同了。 配置创建一个配置文件,写明需要接入的SSID,密码等信息: [plain] view plaincopy5 W2 A" Q# j1 A, _! o7 k
4 V+ e/ v, S+ Q) D" S- t/ v& q# D3 P
- root@(none):/# cat /etc/wpa.conf
- ctrl_interface=/var/run/wpa_supplicant
- network={
- ssid="XXX"
- proto=WPA
- key_mgmt=WPA-PSK
- pairwise=TKIP
- group=TKIP
- psk="
 ASSWORD" ASSWORD" - }
) I" `5 b8 Y2 |) k" w7 a( W# ~/ A! ~
7 d+ H% X) }5 u+ {( {" l. `; C5 l1 @: p) R6 a
其中XXX是路由器的热点名字, psk填写Password, 加密方式TKIP需要根据实际情况填写,不明白可以看我以前的文章,或者直接man。$ }8 r6 b# S$ t6 [
运行先创建一个runtime目录: [plain] view plaincopy
3 X. k. g) r" w' ~! E7 q* h
+ `% p! S9 k1 R9 {5 B5 I# r O( s: H) ~* O! L& B
- root@(none):/# mkdir /var/run/wpa_supplicant , @6 N* [, ?1 g# f
! `2 ~2 |) u3 b# y( L
9 f7 v1 ~0 g& _然后直接在后台运行:
" K: h* m, t% J" C) K( a[plain] view plaincopy- G1 b6 d# i; h+ W* M
4 B4 ^/ E6 {8 U4 U7 s- ^8 [
$ a4 E0 {# T- e+ T& r- root@(none):/# wpa_supplicant -B -iwlan0 -c /etc/wpa.conf
- Successfully initialized wpa_supplicant
- rfkill: Cannot open RFKILL contro[ 172.506937] ieee80211 phy0: rt2x00lib_request_firmware: Info - Loading firmware file 'rt2870.bin'
- l device
- [ 172.527112] ieee80211 phy0: rt2x00lib_request_firmware: Info - Firmware detected - version: 0.29
- [ 173.083412] IPv6: ADDRCONF(NETDEV_UP): wlan0: link is not ready
- root@(none):/# [ 174.937567] wlan0: authenticate with bc:d1:77:a0:4f:3c
- [ 175.073446] wlan0: send auth to bc:d1:77:a0:4f:3c (try 1/3)
- [ 175.082318] wlan0: authenticated
- [ 175.087051] rt2800usb 1-1.2.1:1.0 wlan0: disabling HT/VHT due to WEP/TKIP use
- [ 175.098735] wlan0: associate with bc:d1:77:a0:4f:3c (try 1/3)
- [ 175.108018] wlan0: RX AssocResp from bc:d1:77:a0:4f:3c (capab=0x411 status=0 aid=5)
- [ 175.129960] IPv6: ADDRCONF(NETDEV_CHANGE): wlan0: link becomes ready
- [ 175.136678] wlan0: associated
- [ 176.069997] IPv6: wlan0: IPv6 duplicate address fe80::7edd:90ff:feb2:73b1 detected!
. Z, _( g4 {3 Y0 W
, Z; c- a9 e& J- V2 j, Q+ y. e$ E' V! Y6 h# j6 ~9 `7 W5 q2 S7 e
验证" x9 y! L2 s# i* q
使用wpa_cli看查看连接的状态
* K4 I/ Q" ?4 J8 u. } [plain] view plaincopy- c1 _3 E- n5 R1 m5 _# Z
: Y- \3 F: f# Z
7 k8 p6 v# U5 p; ?+ A- w- root@(none):/# wpa_cli status
- Selected interface 'wlan0'
- bssid=bc:d1:77:a0:4f:3c
- freq=2412
- ssid=XXX
- id=0
- mode=station
- pairwise_cipher=TKIP
- group_cipher=TKIP
- key_mgmt=WPA-PSK
- wpa_state=COMPLETED
- address=7c:dd:90:b2:73:b1
- uuid=1e82e362-f927-544e-aa4d-1a229533944c 0 n+ e" e6 u9 u
9 i( E& O: ~9 H6 P5 Nstatus为COMPLETED那么表示连接上了, 然后我们获取IP地址, 并尝试ping国内的某个网站:
5 L4 g! m* q" Y% P[plain] view plaincopy$ V1 Q' I- q/ S+ @2 G; ^
. R" P' U. W1 w7 ?9 l# \ _
8 v+ v) B; w# J, [! _
- root@(none):/# udhcpc -i wlan0
- udhcpc (v1.24.1) started
- Sending discover...
- Sending select for 192.168.1.112...
- Lease of 192.168.1.112 obtained, lease time 86400
- /etc/udhcpc.d/50default: Adding DNS 192.168.1.1
- /etc/udhcpc.d/50default: Adding DNS 0.0.0.0
-
- root@(none):/# ping meitu.com
- PING meitu.com (42.62.69.156): 56 data bytes
- 64 bytes from 42.62.69.156: seq=0 ttl=42 time=44.499 ms
- 64 bytes from 42.62.69.156: seq=1 ttl=42 time=44.956 ms
- 64 bytes from 42.62.69.156: seq=2 ttl=42 time=43.122 ms
- 64 bytes from 42.62.69.156: seq=3 ttl=42 time=43.387 ms
- 64 bytes from 42.62.69.156: seq=4 ttl=42 time=46.467 ms
- 64 bytes from 42.62.69.156: seq=5 ttl=42 time=46.267 ms
- 64 bytes from 42.62.69.156: seq=6 ttl=42 time=43.843 ms
- ^C
- --- meitu.com ping statistics ---
- 7 packets transmitted, 7 packets received, 0% packet loss
- round-trip min/avg/max = 43.122/44.648/46.467 ms % I/ c2 f" H" M3 R
8 R6 n$ E5 m6 j) g9 [( b- |至此, 我们就完成了基本的配置工作。1 e0 X3 m+ v. G! W5 G
6 F6 ]) l: {7 e- s2 \% |( T1 C+ B7 Q$ o; a4 k1 T: i
; H% n6 h! {' Q, K
本文链接:https://www.ngui.cc/el/1322000.html
% t! F6 l- p! W9 Z Q7 m V2 }1 ~7 U3 ~6 ]8 k& p/ L
|
 |手机版|小黑屋|赛格电脑 华强北 电脑城 南山赛格 龙岗电子世界 龙华电脑城 沙井电脑城 松岗电脑城 pc4g.com
( 粤ICP备16039863号 )
|手机版|小黑屋|赛格电脑 华强北 电脑城 南山赛格 龙岗电子世界 龙华电脑城 沙井电脑城 松岗电脑城 pc4g.com
( 粤ICP备16039863号 )